Ransomware Incidents on the Rise: A Simple Guide to the Latest Mitigation and Recovery Measures
Sep. 21, 2023
Yuzuru Kido

The mass media reports incidents involving ransomware more frequently these days. While the widespread use of the internet has made our lives more convenient, it has also increased the risk of individuals falling victim to cybercrime. So what kind of attack does ransomware perpetrate and what are the key points toward preventing damage from such attacks? This article is an interview with Kenichi Inomata of Hitachi Solutions, Ltd., an expert in ransomware mitigation.
Number of victims in Japan: Increasing 60% from the previous year
──What exactly is ransomware?
Inomata: Ransomware is a portmanteau of "ransom" and "malware" (software that performs malicious actions). Criminal groups use ransomware to infect the computers of businesses and individuals, rendering the computers unusable by encrypting the data on the computer and demanding a ransom from the victims.
Around 2017, ransomware known as "WannaCry" rapidly infected hundreds of thousands of computers worldwide and hence earned widespread notoriety. In recent years, there have been cases of ransomware not only encrypting data but also stealing data and threatening to make the data public if the ransom is not paid.
In the past, most ransomware attacks were random: they targeted an unspecified number of individuals, enticing the victims to click a link in the body of an e-mail. However, recently we have seen a pattern in which they target specific companies.

──Are ransomware victims increasing?
Inomata: According to statistics from the National Police Agency, there were 230 victims of ransomware in Japan in 2022—a 57.5% increase from the previous year. Not only were large companies (27% of the total) affected, but small and medium-sized companies (53% of the total) and other organizations, such as NPOs (20% of the total), were also affected.
Looking at the time required to recover from such attacks, some computers were restored immediately or in less than a week (26% of all cases), but the majority of cases took more than a week, and in some cases, more than two months. Furthermore, while some attacks (24% of all attacks) required less than 1 million yen to investigate the cause and restore the computers, 46% of all attacks required more than 10 million yen.
Backups for security measures
──To prevent ransomware attacks, what mitigation measures should be part of regular security practices?
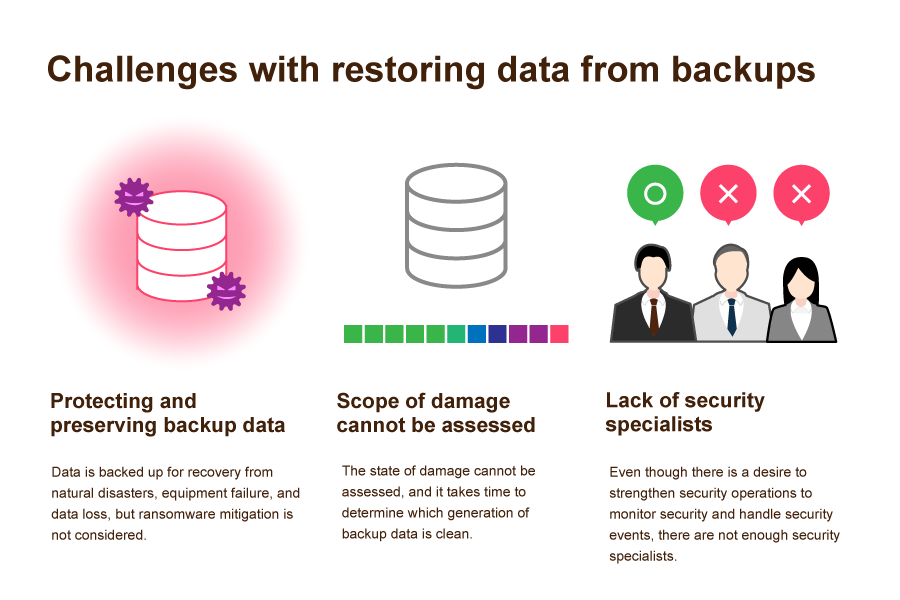
Inomata: There are several mitigation measures that can be taken, such as not clicking links in suspicious e-mails, setting strong passwords, and installing anti-virus software, but one important measure is to back up data. Even if a company is hit by ransomware, if the backup data can be restored, the systems necessary for business can resume operations. In fact, many companies have backup measures in place. However, according to statistics from the National Police Agency, although 83% of those affected had backups, only 19% were able to restore their data.
Cases of failure to restore data can be attributed to not being aware of security considerations due to the fact that backup data was not protected or that multiple generations of backup data were not created. In a ransomware attack, it is possible that the backup data itself is encrypted by the malware and cannot be restored.
──What should someone do if they fall victim to ransomware?
Inomata: If one should be unfortunate enough to be infected, the first step is to contain the spread of the malware and limit the damage by, for example, disconnecting any compromised computer from the network. Next, identify the extent of the damage, perform a clean reinstall of the operating system, and then restore/recover data. The key to rapid business restoration lies in how quickly the extent of the damage can be identified for containment.
Many companies lack security specialists, so they have to find a security vendor after the damage occurs, and hence it takes a long time to recover from an attack. For a rapid response, best security practices suggest regular monitoring. If a company does not have enough security specialists, they should outsource the work to a security vendor before they become a victim.
Rapid recovery with encrypted file identification
──What are the ways that one can back up and restore data?
Inomata: One example is the services for data recovery by Hitachi Solutions, which provides three elements for secure backup and rapid data recovery.
- Protects backup data by saving it in a safe location
- Quick detection and containment of ransomware infections
- Uniform support all the way through to restoration work
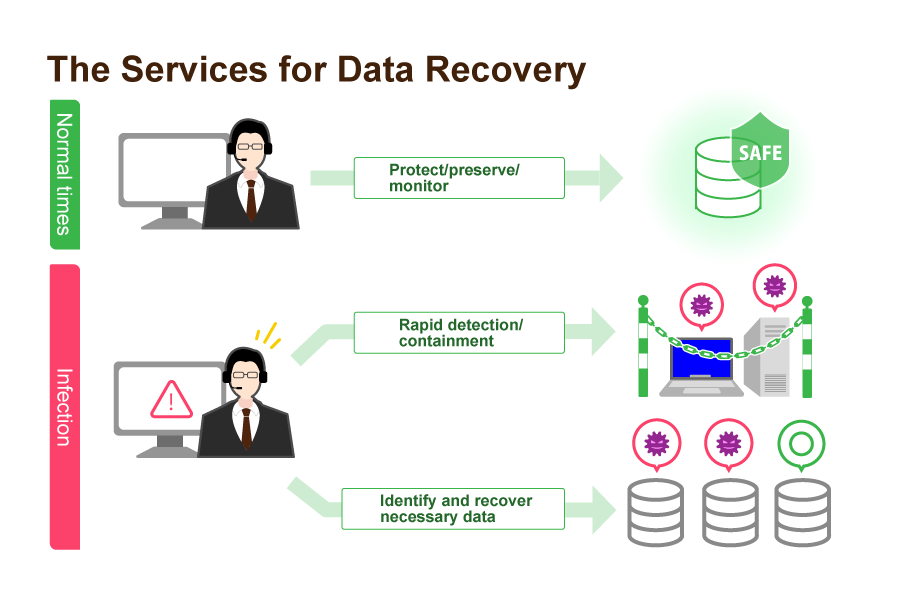
Backup data is stringently protected and properly managed in terms of generations (a backup method that saves not only the latest data but also earlier data). Daily monitoring ensures rapid detection and containment in the event of infection. This is a one-stop support service that quickly identifies the extent of the damage and the data that needs to be recovered, confirms the veracity of the data in a clean environment, and then restores the data.
── What is the biggest feature of the services for data recovery?
Inomata: Once an infection is detected, the approximate infected device and the scope of infection can be roughly guessed, but the software goes one step further by identifying the affected files using an investigation tool based on our proprietary technology.
Files encrypted with ransomware are characterized by the random arrangement of data. By checking the degree to which the data is erratically scattered within the file, the investigation tool identifies the encrypted file.
Once the extent of the damage is identified, decisions can be made quickly on whether to recover all the data, partially recover the data, or rebuild the system, thus shortening the time required to restore business operations.
Importance of cyber resilience
──So how quickly infections can be detected and the extent of damage identified is important.
Inomata: Conventional security measures dictate "complete protection" to defend against external attacks by strictly separating internal and external networks. However, as the use of external networks has increased due to the spread of cloud computing and other factors, "zero-trust security," which does not trust communications between internal and external networks, has grown in popularity.
And cyber resilience considers how to enable business continuity based on the premise that cyberattacks will occur. Thus, the services were born.

──How is cyber resilience achieved?
Inomata: To achieve cyber resilience, four types of capabilities are required: anticipate, withstand, recover from, and adapt to adverse conditions, stresses, attacks.
In the future, cyberattacks are expected to become more advanced and sophisticated as technology advances. Every company will first need to accurately ascertain its current level of security, determine which capabilities are weak according to business characteristics and security policy, and constantly make improvements.
Hitachi Solutions is also committed to expanding security solutions that enhance the respective strengths of cyber resilience by leveraging our proprietary technologies and extensive human capital.



