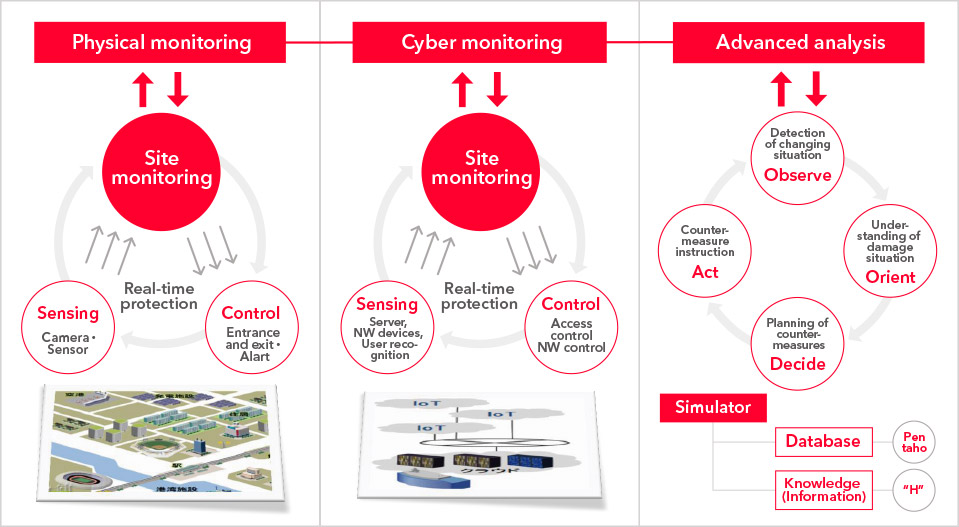
Security
Hitachi’s solutions thoroughly protects social infrastructure systems from security threats.
We offer a comprehensive security solution that covers everything from consulting in the upstream stages to the monitoring of operation, resulting in robust, multi-layered defenses.
In the current digital age, services in various business areas need to run uninterrupted, 24 hours a day, 365 days a year. While progress has been made in providing services more efficiently through technologies such as IoT, the methods of cyber attacks have become increasingly diverse and sophisticated—even verging on cyberterrorism.
That’s why security within the system is essential. But that alone won’t guarantee total protection.
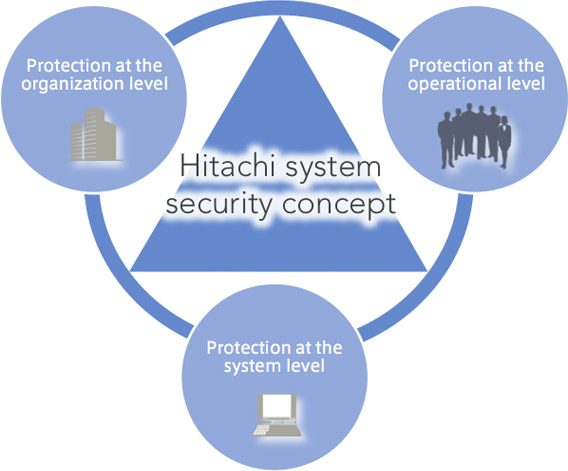
Hitachi’s security approach
At Hitachi, we understand that rigorous security involves continuous improvements, which require additional protection at both the operational and organizational levels. With this understanding, Hitachi employs a security approach that focuses on four key attributes: Hardening (strong protection), Adaptive (flexibility), Responsive (dealing rapidly) and Cooperative (working with clients based on their needs). Under the principals of this security approach, we deliver a comprehensive defense solution that includes organizational, operational and systematic protection.
Hitachi also works closely with clients to co-create and develop scalable security measures, while offering a full range of services that cover the entire value chain—from consulting in the upstream stages to the monitoring of operations. At Hitachi, we’re committed to the protection of our social infrastructure systems. Together with our clients, we’ll continue to safeguard our future from the security threats of today and tomorrow.
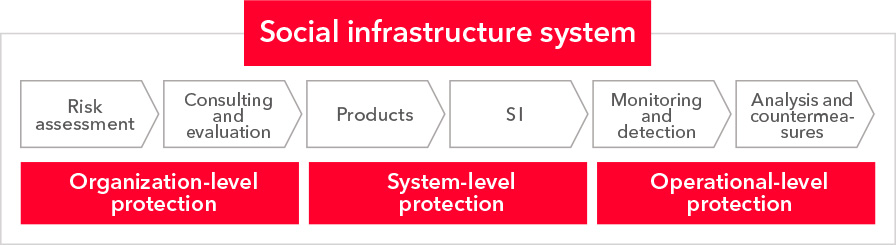
We developed our security approach based on our wealth of experience in offering security services.
Hitachi has a long history of building social infrastructure systems. Based on the concept of a value chain, we have been providing a total solution ranging from consulting in the upstream stage to operations. In these initiatives, we’ve always focused on one question: What do customers need in order to provide their services with peace of mind? At Hitachi, we have continued to propose our security solution to social infrastructure companies based on a thorough understanding of their on-site operations.
Meanwhile, Hitachi also has a track record of operating IT infrastructure for approximately 300,000 internal users within the Hitachi Group. Through this initiative, we are continuing to add to our extensive knowledge on how to deal with cyber attacks.
Hitachi’s security approach was established on the basis of this experience and our history of safeguarding public and private institutions against threats.
Along with our cultivated capabilities in cyber and physical technologies, we’ll continue to work collaboratively with our clients to deliver comprehensive security solutions.

We customize the details of each solution based on our client’s needs, while providing systems for a broad range of fields .
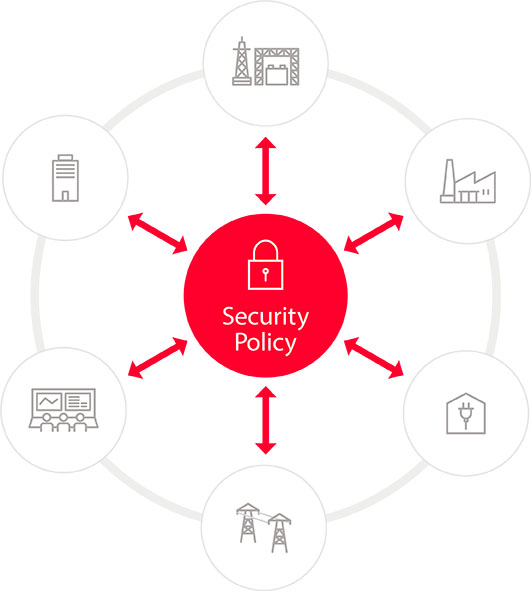
Security Measures for Power Control Systems
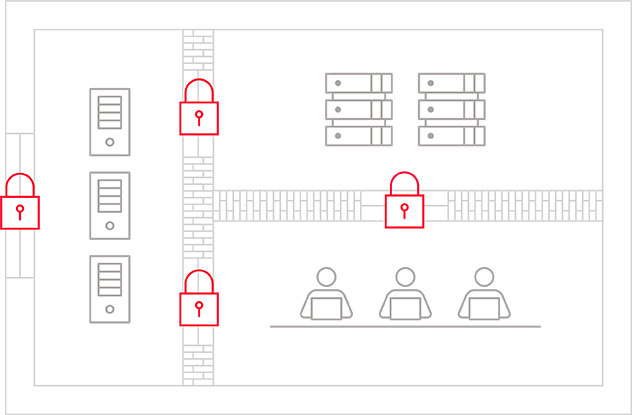
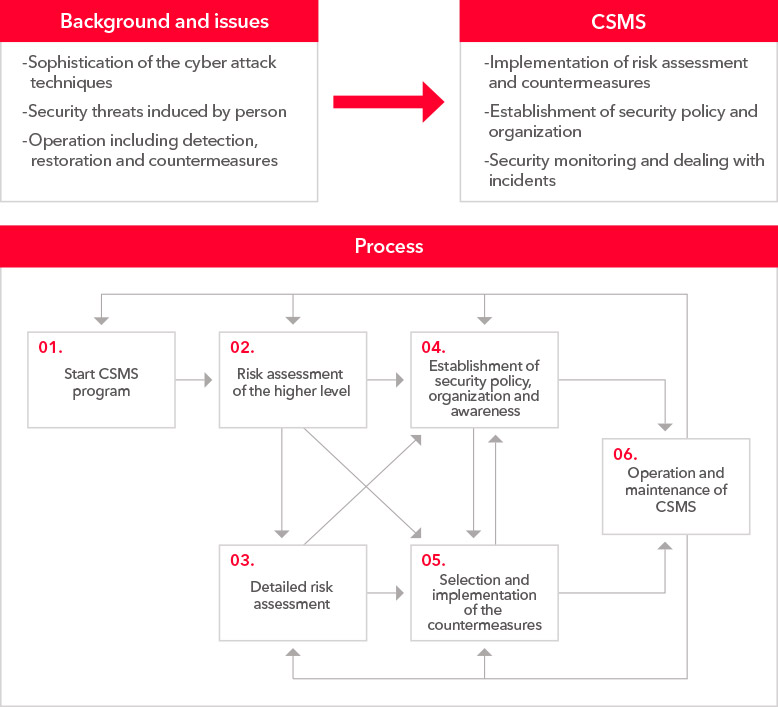
We identify and anticipate every single risk in the entire large-scale system. We then establish a security policy based on developed countermeasures, which encompass the physical, informational and control systems. Through this structure, we’re able to protect infrastructures operating 24 hours a day, 365 days a year.
Security Measures for Information Systems
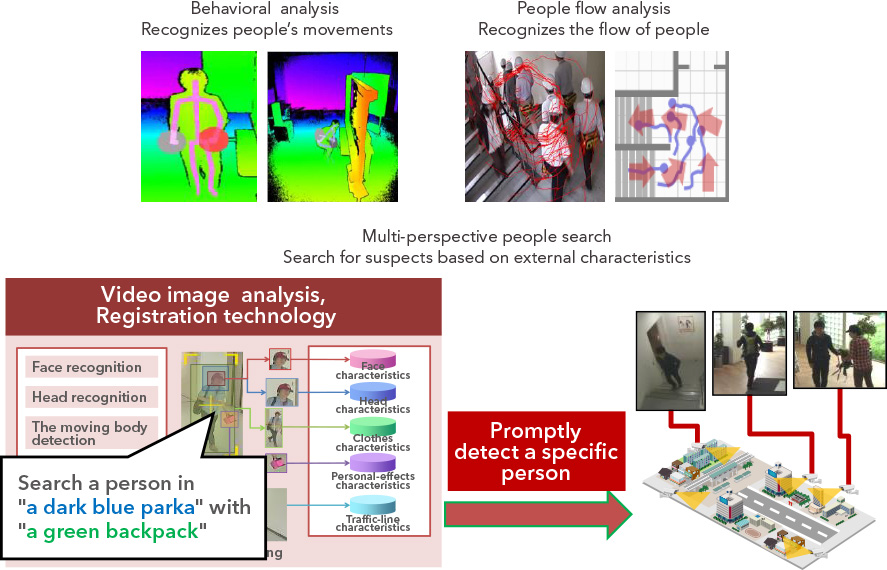
Information leakage is a reality of today’s digital age. Amid increasingly diverse and sophisticated cyber attacks, vulnerabilities in IT infrastructures are being discovered every day. But that doesn’t mean risks are unavoidable. At Hitachi, we protect IT infrastructures with a defense-in-depth framework—integrating perspectives ranging from entrance and exit, to diffusion countermeasures. By doing so, we safeguard information assets that are the lifeline to any company.