By linking a wide variety of devices and people, the Internet of Things (IoT) is driving a major shift in public & business activity toward the digital world and is generating new value. This is offset by new risks, such as cyber-attacks, which have been involved in a series of incidents resulting in breakdowns in the functioning of important social infrastructure and threats to the continued existence of businesses. In response to these risks, Hitachi provides powerful support for safe & secure public systems & businesses by engaging in collaborative creation with social infrastructure operators and numerous other organizations. Here, Takeshi Miyao, who is the general manager of the Security Businesses Division, explains the thinking behind this, together with some practical examples.
The social infrastructure essential to life and business includes things like finance and healthcare as well as electric power, telecommunications, gas, water, and railways. The essential services that underpin industry and our way of life must operate continuously, 24 hours a day, 365 days a year. That this social infrastructure might one day suddenly cease to function is hard to believe, yet it is now starting to become a reality.
The reason for this is the rise of cyber-attacks on social infrastructure. Among the most serious examples are targeted cyber-attacks that aim unremittingly at a specific objective. The methods deployed in such attacks are highly skillful and increasingly come in a form that cannot be dealt with by conventional anti-virus measures. Once established, an infection opens up a system to remote manipulation so that it can be made to do things at the whim of the attacker.
Internationally, cases of such terroristic attacks have been reported. An incident in December 2015 involving an electric power utility in the Ukraine is a typical example. The attack caused major disruption to the population, triggering a major outage that lasted 6 hours and affected 1.4 million households.
Cyber-attacks also cause serious damage to corporate management. When POS terminals at the stores of Target, a major US retailer, became infected with malware, it resulted in the loss of 40 million people's credit card usage data and information on 70 million customers. In addition to the payment of a great sum of money in compensation, the incident also damaged the company's sales and stock price, and led to the resignation of its CEO for reasons of accountability.
So why are there so many cases of this sort of damage occurring? Advances in the Internet and other areas of IT are one background factor. The control systems used by social infrastructure in the past tended to be isolated from the outside world. Nowadays, however, rather than remaining unconnected, these systems are increasingly being configured in such a way that there is potential for indirect connection to the Internet via peripheral devices. Once control systems are connected to a network, the benefits extend globally, enabling centralized administration and more efficient operation.

The nature of the attackers, too, is changing. Up until a decade ago, most were hackers who were in it for the fun and wanted to demonstrate their technical prowess. The damage they caused was comparatively light, such as interfering with the operation of PCs. Now, however, attacks have become a form of organized crime, being aimed at disrupting people's lives, and with objectives such as information or financial fraud. A wide variety of tools for cyber-attacks are available on the black market, creating an environment in which attacks can be launched at minimal cost. Meanwhile the large potential rewards from a successful attack provide strong motivation for attackers.
Those charged with defending against such attacks face a number of challenges. Along with the difficulty of deciding how far security measures should be taken, attacks come in many different shapes and forms. Being ignorant of what capabilities their adversaries may possess, defenders are forced to adopt a wide variety of defenses. In other words, cybersecurity is a field in which the attacker has an overwhelming advantage. Adopting patchwork defenses still leaves blind spots for attackers to discover.
It is crucial for security measures that a grand design be devised that takes a broad view of the situation. This needs to be complemented by establishing the systems required to get defenses in place, and by conducting ongoing monitoring and response. Also essential is to have in place the organizational practices required for maintaining or recovering business operations in the event of an incident. Hitachi's approach to security measures is to provide comprehensive support for these activities.
Hitachi's greatest strength is its ability to deliver a "trinity" of organization-level, system-level, and operational-level protection in accordance with its Hitachi system security concept.
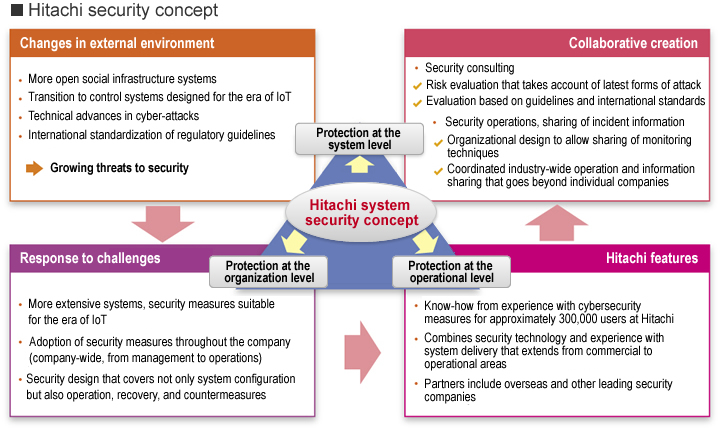
In addition to know-how in security operation, a strength of Hitachi is the value it adds through collaborative creation with customers and other partners. Hitachi provides comprehensive security that delivers protection at the organization, system, and operational levels, and that can deal with changing circumstances, including the latest regulations and guidelines as well as technical advances in cyber-attacks.
For systems, Hitachi supplies consulting and risk evaluation based on international standards that extends from commercial to operational areas and takes account of the latest forms of attack. Hitachi also designs and builds optimal systems that include physical security measures for defending against unauthorized operation by insiders as well as monitoring and defending against network-based cyber-attacks.
For organizations, Hitachi supports the design of organizational practices that take account of everything from the training and deployment of staff with expertise in security, to the establishment of practices for information sharing and coordination, and the operational optimization of workplace activities and risk management from a commercial perspective. This involves identifying vulnerabilities within the organization, including impacts on systems, work, or services, and working with the customer to devise methodologies for overcoming these vulnerabilities.
At the operation level, Hitachi supports the design and adoption of effective operational rules by drawing on knowledge and know-how based on its own security operations with its approximately 300,000 employees. In cases where the customer's own operation is impractical, Hitachi supplies services that support risk monitoring and management, routine log analysis, and incident response and recovery procedures. One of Hitachi's strengths is its large number of support bases that are distributed globally. Because these bases play a central role in responding to threats, they can offer timely local support.
This "trinity" of strengths can be used to provide multi-layered defenses by combining a wide variety of operating practices and countermeasures for different attacker skill levels. In doing so, Hitachi offers powerful support for building social infrastructure that is resilient to attack.
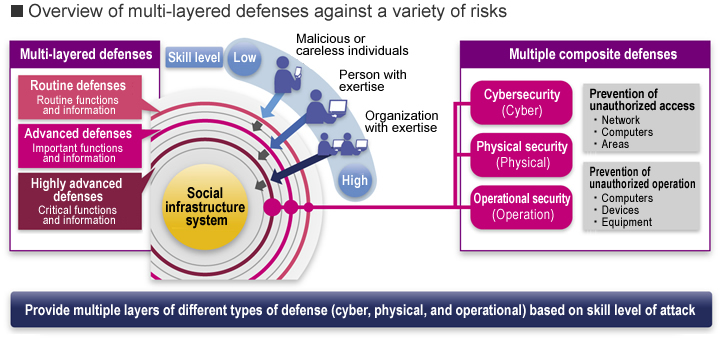
Hitachi helps build social infrastructure that is resilient to attack through multi-layered defenses that provide both cybersecurity measures for different attacker skill levels and physical security measures, while also facilitating the optimization of operating practices for these security measures.
What makes this possible is Hitachi's many years of experience supplying social infrastructure at a global level and the total support it offers, including infrastructure operation. This has included many construction and operation projects in countries around the world, not just Japan, such as power plant infrastructure, plants for gas companies, and traffic management systems for railway operators. In doing so, Hitachi has built up knowledge of industry-specific challenges and numerous customer businesses that it has formalized in the form of skills. This understanding of customer systems and practices enables optimal security design.
Hitachi also has a longtime involvement with security technology. Having recognized the importance of cybersecurity from the early days of the Internet, the Hitachi Incident Response Team (HIRT) was established in 1998 to work on the detection and analysis of viruses and other malware. The benefits of this experience are made widely available to customers. Hitachi is also working on fusing its security technology with its big data, artificial intelligence (AI), and other information technology (IT). Future possibilities include the use of data as a basis for identifying previously unknown threats and the automation of proactive countermeasures.
The value created through collaborative creation with customers and other partners is another major strength. In the case of security design, Hitachi pays careful attention to customer needs and requirements, and strives to implement more appropriate and effective countermeasures. It is also enhancing and expanding its systems and services by building an eco-system with partners who have strengths in particular fields. In practice, this includes working with security vendors that operate internationally, and utilizing their knowledge to collect and analyze information on the latest threats.
Hitachi is also taking steps to keep pace with international trends and developments. One example is a risk assessment service that is provided in accordance with a cybersecurity management system (CSMS) for industrial automation and control systems being worked on by the International Electrotechnical Commission (IEC). Support is provided for countermeasures that satisfy the requirements of Japan's Basic Act on Cybersecurity that came into effect in January 2015. Hitachi is also involved in activities that look at the broader picture, including drawing on its technology and knowledge to participate in formulating the Cybersecurity Management Guidelines of the Ministry of Economy, Trade and Industry.

Hitachi supplies solutions to problems based on a grand design that takes a broad view of the situation. This provides greater value than is possible with individual products and services on their own.
With its extensive experience, Hitachi is contributing to security measures for a wide variety of social infrastructure. Security measures for power plants in Japan that take account of the entire value chain are one such example. This involves both cyber and physical security measures based on consulting and risk assessment. Specifically, the risk of system intrusions is minimized by combining cyber and physical security to provide multiple gateway layers through which any attack must pass. Hitachi has also established security policies that provide reliable protection for control systems, providing an operational service that extends from risk monitoring to detection, analysis, and response. By putting a management system in place, this has significantly improved the security of infrastructure.
Overseas, a trial using video surveillance systems for facilities management is being undertaken in Asia. The aim is to support comprehensive risk management by using physical security as a starting point for the provision of cybersecurity.
With the emergence of the IoT being accompanied by the geographical expansion and ongoing evolution of a variety of systems, the future will see a continued increase in the threat of cyber-attacks that target critical social infrastructure and corporate systems. How can the risk of cyber-attack be dealt with in a connected society? Hitachi intends to draw on the experience and knowledge it has acquired from the implementation and operation of a large number of social infrastructure systems to continue providing safe and secure social infrastructure systems by supporting the business operations of its customers and by engaging in collaborative creation with a large number of social infrastructure operators and other organizations.
Release Date: June 2016







